Secure Collaboration in Global Supply Chain Management
One of the fundamental problems in supply chain management in general is that of finding the right trade-offs between information sharing and keeping one’s distance towards potential competitors.
Zeng et al. did a literature review to collect some of the current insights on how to solve this problem.
Collaboration in product design and supply chain environment
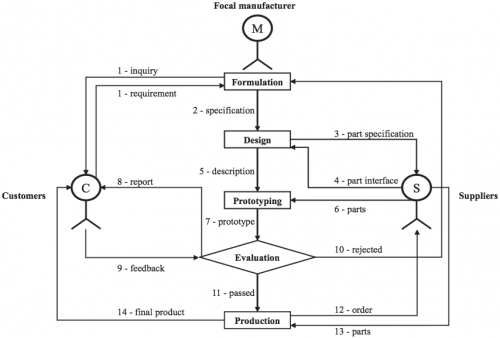
Figure 1: Collaborative Product Development Process (Zeng et al., 2012)
Figure 1 shows a typical process from problem formulation up to delivery of the finished product. This process can be decomposed into: collaborative product development (CPD), design chain management (DCM) and supply chain management (SCM).
Collaboration conflicts
Several conflicts threaten the viability of the collaboration. These are all related to the information which is interchanged by the stakeholders.
Figure 2 shows the information flow.
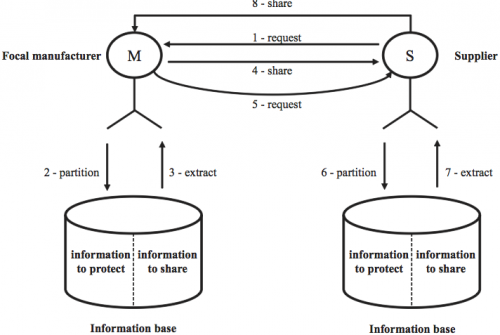
Figure 2: Information Flow between Supply Chain Participants (Zeng et al., 2012)
This information can be divided into information to protect and information to share.
Figure 3 lists some of the relevant information.
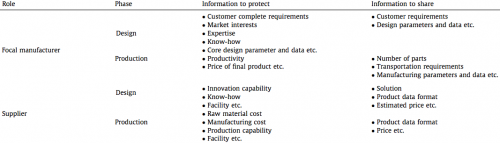
Figure 3: Information to Protect and Information to Share (Zeng et al., 2012)
Securing collaboration
Figure 4 summarizes the problem analysis and the corresponding conclusions the authors draw.
![]()
Figure 4: Problem Analysis and Potential Solutions (Zeng et al., 2012)
The authors suggest and elaborate on four categories to secure collaboration:
- Computer security and privacy technologies
Which consists of measures for access control and secure multi-party computation, where computations can be done on multiple datasets without revealing the underlying information. Furthermore privacy-preserving location-based services are summarized here. - Information partitioning
This contains the aspects of document classification and risk management. - Contract management
- Partner relationship management
Here the authors include trust management and innovation capability and reverse engineering mitigation.
Last but not least figure 5 summarizes the current state of the art for the above mentioned problems and potential future research directions.
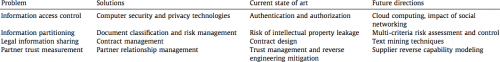
Figure 5: Future Research Directions on Secure Collaboration (Zeng et al., 2012)
Conclusion
The authors take the view of a computer scientist and find technical solutions (like secure multi-party computation) to fight supply chain problems.
One of the first things that came to my mind: “One cannot use technology to solve social problems.”
I do think that those measures should be pursued further in research as well as business. But the first steps have to be done by describing and defining their individual information buckets, by answering the strategic question: What information is core to our business and should be protected and what can be shared?
Zeng, Y., Wang, L., Deng, X., Cao, X., & Khundker, N. (2012). Secure collaboration in global design and supply chain environment: Problem analysis and literature review Computers in Industry, 63 (6), 545-556 DOI: 10.1016/j.compind.2012.05.001







Add new comment